Zadara Cloud Services Policies
Overview
Zadara Cloud Services Policies define the permissions for accessing Zadara Cloud Services functionality. For each project available to a user, one or more Zadara Cloud Services Policies and a single Zadara Cloud Services Role are assigned. If the role of the user does not match the role type of any of the APIs included in the policy, then the user cannot perform these APIs, even if the policy which includes these APIs was assigned to the user.
Whenever a new user is created via the GUI, a FullAccess policy is the suggested default Zadara Cloud Services policy. When a new user is created via the API/CLI, FullAccess is automatically assigned Zadara Cloud Services policy. This policy provides full access to all of the services that each Zadara Cloud Services role granted in the past, prior to v5.3.4.
Note
In the ZCS GUI, Zadara Cloud Services policy is shown in the Identity & Access > Symp API Policies view.
Working with Zadara Cloud Services Policies
Zadara Cloud Services policies can be assigned while creating a user on the Permissions tab of the Create User wizard, or on the Manage Permissions dialog for an existing user. For more information on assigning policies to users, see Creating Users.
Note
If a Zadara Cloud Services policy is assigned to a user while the user is in the middle of a session, it will not take effect until the user first logs out of the current session and then logs in again to a new session.
Assigning Permissions for Creating a VM
As an example of how to use policies to allow certain functionality, the following section explains how to use Zadara Cloud Services policies to grant the permissions needed by a user to create a VM.
A Member user with only VMFullAccess rights, grants permission to create a VM and select an Instance Type, but there are no permissions to view the following entities:
Image
Storage Pool
Subnet
A Member user with legacy permissions providing full access to all Zadara Cloud Services member functionality, can create a VM. All of the fields in the Create VM dialog, including Image, Storage Pool, and Subnet are available to these users.
A Member user assigned the VMFullAccess Zadara Cloud Services policy together with the ZadaraReadOnlyAccess policy can also create a VM.
The VMFullAccess Zadara Cloud Services policy permits the creation of a VM and the selection of any Instant Type.
The ZadaraReadOnlyAccess Zadara Cloud Services policy permits the viewing and selecting of any entity available to the legacy Member user, including the following:
Images
Storage Pools
Subnets
A Member user assigned the VMFullAccess Zadara Cloud Services policy together with the following read-only Zadara Cloud Services policies can also create a VM:
The VMFullAccess Zadara Cloud Services policy permits the creation of a VM and the selection of an Instant Type.
The ImagesReadOnlyAccess Zadara Cloud Services policy permits the viewing and selecting of Images.
The StorageReadOnlyAccess Zadara Cloud Services policy permits the viewing and selecting of Storage Pools.
The VPCReadOnlyAccess Zadara Cloud Services policy permits the viewing and selecting of Subnets.
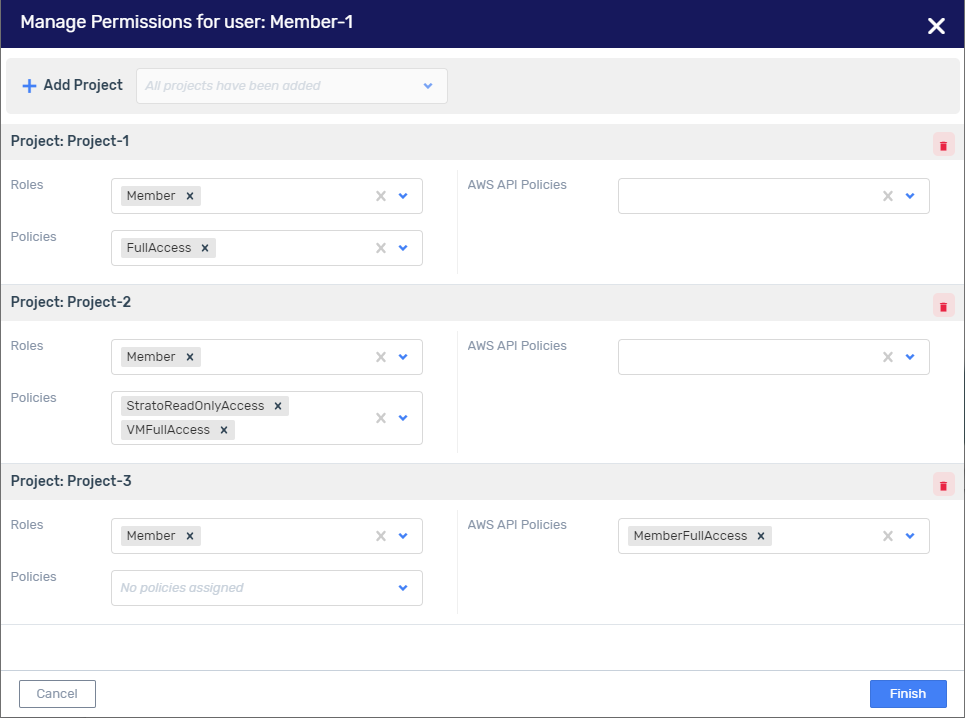
Assigning Permissions for Multiple Projects to a Single User
The following section explains how to use Zadara Cloud Services policies to assign multiple projects to a single user. This can be done when creating the user or by managing permissions of an existing user. For example, to assign permissions for only Zadara Cloud Services functionality (but not AWS API functionality) for each of three different projects, the configurations below should be made.
Projects:
Project-1 - Full legacy Member role permissions
Project-2 - Permissions to create VMs and many other actions concerning VMs
Project-3 - To be determined
In the Manage Permissions for user view, the following information should be configured:
Roles - Verify that the Member role has been assigned to each project.
Note
It is strongly recommended not to assign different roles to the same user for different projects.
Policies - Each Project should be assigned the following Zadara Cloud Services policies:
Project-1 - Select the
FullAccesspolicyto grant Member legacy permissions.Project-2 - Select the
VMFullAccessandStratoReadOnlyAccessto grant permissions to create a VM, including viewing Images, Storage Pools and Subnets, access to which is necessary when creating a VM.Project-3 - Leave empty until User-1’s responsibilities for this project have been determined.
Note
As long as at least one project has both assigned a Zadara Cloud Services Role and Policy, the user’s permissions for other projects need not be completely defined.
AWS API policies - Verify the MemberFullAccesspolicy is removed from each of the projects.
Click Finish.
List of Managed Zadara Cloud Services Policies
Zadara Cloud Services Policies basically consist of two policies per service, one for FullAccess of all the service’s APIs, and one for ReadOnly access of all the service’s APIs.
FullAccess – a policy which provides full access to all Zadara Cloud Services APIs based on the user’s role.
ReadOnlyAccess - a policy which provides read-only access to all Zadara Cloud Services APIs based on the user’s role.
Exceptions to this rule are:
The Identity Service which has two additional policies:
IdentityBasicUsage - which provides access to those identity entities available to a Member user.
IdentitySTSAssumeRole - which provides the ability to obtain an IAM role using the ‘assume-role’ API.
The Snapshot service which has three sets of FullAccess and ReadOnlyAccess policies, one set for each of the following:
Snapshot
RemoteSnapshot
RemoteVMSnapshot
The VM service which has two sets of FullAccess and ReadOnlyAccess policies, one set for each of the following:
VM
VMSnapshot
The table below summarizes all Zadara Cloud Services Policies with their descriptions and the roles for which they are enforced. To see the actual content of a policy go to the Identity & Access > Symp API Policies view, and click on the requested policy.
Zadara Cloud Services Policy |
Description |
Available to: |
|
|---|---|---|---|
AlarmsFullAccess |
Provides full access to all alarms APIs |
All ZCS roles |
|
AlarmsReadOnlyAccess |
Provides read-only access to all alarms APIs |
All ZCS roles |
|
AutoScalingFullAccess |
Provides full access to all autoscaling-group APIs |
All ZCS roles |
|
AutoScalingReadOnlyAccess |
Provides read-only access to all autoscaling-group APIs |
All ZCS roles |
|
CRSFullAccess |
Provides full access to all container registry APIs |
All ZCS roles |
|
CRSReadOnlyAccess |
Provides read-only access to all container registry APIs |
All ZCS roles |
|
CertificateManagerFullAccess |
Provides full access to all certificate APIs |
All ZCS roles |
|
CertificateManagerReadOnlyAccess |
Provides read-only access to all certificate APIs |
All ZCS roles |
|
CloudWatchFullAccess |
Provides full access to all cloudwatch APIs |
All ZCS roles |
|
CloudWatchReadOnlyAccess |
Provides read-only access to all cloudwatch APIs |
All ZCS roles |
|
ConversionsFullAccess |
Provides full access to all conversion APIs |
All ZCS roles |
|
ConversionsReadOnlyAccess |
Provides read-only access to all conversion APIs |
All ZCS roles |
|
DBCFullAccess |
Provides full access to all DB cluster APIs |
All ZCS roles |
|
DBCReadOnlyAccess |
Provides read-only access to all DB cluster APIs |
All ZCS roles |
|
DBSFullAccess |
Provides full access to all DB APIs |
All ZCS roles |
|
DBSReadOnlyAccess |
Provides read-only access to all DB APIs |
All ZCS roles |
|
EngineFullAccess |
Provides full access to all engine APIs |
All ZCS roles |
|
EngineReadOnlyAccess |
Provides read-only access to all engine APIs |
All ZCS roles |
|
ExternalEndpointFullAccess |
Provides full access to all external-endpoint APIs |
All ZCS roles |
|
ExternalEndpointReadOnlyAccess |
Provides read-only access to all external-endpoint APIs |
All ZCS roles |
|
EventsAccess |
Provides access to all events APIs |
All ZCS roles |
|
FullAccess |
Provides full access to all Zadara Cloud Services APIs based on user’s scope |
All ZCS roles |
|
GuestnetToolFullAccess |
Provides full access to all guestnet-admin-tool APIs |
All ZCS roles |
|
GuestnetToolReadOnlyAccess |
Provides read-only access to all guestnet-admin-tool APIs |
All ZCS roles |
|
HotUpgradeFullAccess |
Provides full access to all hot-upgrade APIs |
Admin |
|
HotUpgradeReadOnlyAccess |
Provides read-only access to all hot-upgrade APIs |
Admin |
|
IdentityBasicUsage |
Provides access to basic identity entities operations. |
All ZCS roles |
|
IdentityFullAccess |
Provides full access to identity APIs |
All ZCS roles |
|
IdentityReadOnlyAccess |
Provides read-only access to identity APIs |
All ZCS roles |
|
IdentitySTSAssumeRole |
Provides the ability to obtain an IAM role using the ‘assume-role’ API |
All ZCS roles |
|
ImagesFullAccess |
Provides full access to all image APIs |
All ZCS roles |
|
ImagesReadOnlyAccess |
Provides read-only access to all image APIs |
All ZCS roles |
|
InspectorFullAccess |
Provides full access to all inspector APIs |
Admin |
|
InspectorReadOnlyAccess |
Provides read-only access to all inspector APIs |
Admin |
|
KubernetesFullAccess |
Provides full access to all Kubernetes APIs |
All ZCS roles |
|
KubernetesReadOnlyAccess |
Provides read-only access to all Kubernetes APIs |
All ZCS roles |
|
LbaasFullAccess |
Provides full access to all LBaaS APIs |
All ZCS roles |
|
LbaasReadOnlyAccess |
Provides read-only access to all LBaaS APIs |
All ZCS roles |
|
MapReduceFullAccess |
Provides full access to all map-reduce APIs |
All ZCS roles |
|
MapReduceReadOnlyAccess |
Provides read-only access to all map-reduce APIs |
All ZCS roles |
|
MetricsAccess |
Provides access to all metrics APIs |
All ZCS roles |
|
NFSFullAccess |
Provides full access to all NFS APIs |
All ZCS roles |
|
NFSReadOnlyAccess |
Provides read-only access to all NFS APIs |
All ZCS roles |
|
NodesFullAccess |
Provides full access to all node APIs |
Admin |
|
NodesReadOnlyAccess |
Provides read-only access to all node APIs |
Admin |
|
ObjectStoresFullAccess |
Provides full access to all object-store APIs |
All ZCS roles |
|
ObjectStoresReadOnlyAccess |
Provides read-only access to all object-store APIs |
All ZCS roles |
|
ProtectionFullAccess |
Provides full access to all protection APIs |
All ZCS roles |
|
ProtectionReadOnlyAccess |
Provides read-only access to all protection APIs |
All ZCS roles |
|
QuotasFullAccess |
Provides full access to all quota APIs |
All ZCS roles |
|
QuotasReadOnlyAccess |
Provides read-only access to all quota APIs |
All ZCS roles |
|
RemoteSnapshotFullAccess |
Provides full access to all remote-snapshot APIs |
All ZCS roles |
|
RemoteSnapshotReadOnlyAccess |
Provides read-only access to all remote-snapshotAPIs |
All ZCS roles |
|
RemoteVMSnapshotFullAccess |
Provides full access to remote VM Snapshot APIs |
All ZCS roles |
|
RemoteVMSnapshotReadOnlyAccess |
Provides read-only access to remote VM Snapshot APIs |
All ZCS roles |
|
Route53FullAccess |
Provides full access to all Route53 APIs |
All ZCS roles |
|
Route53ReadOnlyAccess |
Provides read-only access to all Route53 APIs |
All ZCS roles |
|
SnapshotFullAccess |
Provides full access to all local compute-snapshot APIs |
All ZCS roles |
|
SnapshotReadOnlyAccess |
Provides read-only access to all local compute-snapshot APIs |
All ZCS roles |
|
StorageFullAccess |
Provides full access to all storage APIs |
Admin |
|
StorageReadOnlyAccess |
Provides read-only access to all storage APIs |
All ZCS roles |
|
StratoReadOnlyAccess |
Provides read-only access to all Zadara Cloud Services APIs based on user’s scope |
All ZCS roles |
|
VMFullAccess |
Provides full access to VM APIs |
All ZCS roles |
|
VMReadOnlyAccess |
Provides read-only access to VM APIs |
All ZCS roles |
|
VMSnapshotFullAccess |
Provides full access to VM Snapshot APIs |
All ZCS roles |
|
VMSnapshotReadOnlyAccess |
Provides read-only access to VM Snapshot APIs |
All ZCS roles |
|
VPCFullAccess |
Provides full access to all VPC APIs |
All ZCS roles |
|
VPCReadOnlyAccess |
Provides read-only access to all VPC APIs |
All ZCS roles |
|
VolumesFullAccess |
Provides full access to all volume APIs |
All ZCS roles |
|
VolumesReadOnlyAccess |
Provides read-only access to all volume APIs |
All ZCS roles |
Notes:
It is currently possible to assign a Zadara Cloud Services policy to a user, for whose role, the APIs in this policy will not be permitted. For example, it is possible to assign the NodesFullAccess policy to Member users, even though the APIs in this policy will not be permitted for Members. In a future release, this invalid assignment will be prevented.
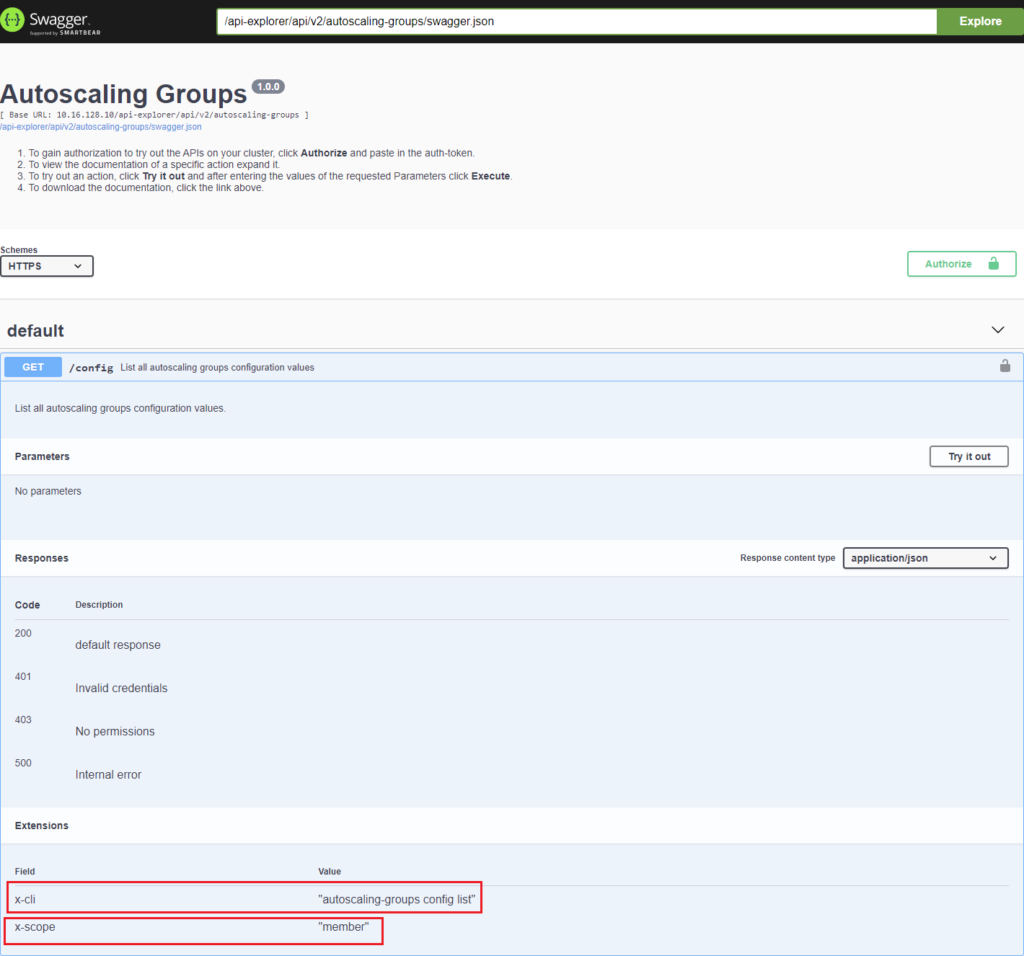
A Zadara Cloud Services policy which is permitted for a Member or Tenant Admin role, may nevertheless include some APIs/CLIs which are not permitted for that role. For example, the VMFullAccess policy whose APIs/CLIs are permitted for all roles, including the Member role, contains the API, ‘vm live-migrate’ which migrates VMs from one node to another. This action can be performed only by a Zadara Admin user. To determine the role for which specific APIs of a Zadara Cloud Services policy are permitted, access the API Explorer for the service covered by the policy and open the API, as shown below.
In the Extensions section at the bottom of the window, the x-cli field displays the name of the CLI while the x-scope field displays the role with the least amount of permissions which may use this CLI. (e.g. ‘member’ has less permissions than ‘tenant_admin’). If x-scope = ‘all’ permissions are not required to perform the CLI.