Managing Cloud Logs¶
Command Center maintains a centralized cloud level event log which can be utilized for detailed infrastructure monitoring and troubleshooting. Log event can be viewed and searched from the Command Center Central Log tab. Events may also be shipped to an external syslog daemon for 3rd party application based event monitoring.
Searching And Filtering Logs¶
Cloud log can be searched and specific events extracted using the Command Center filtering functionality. To search for specific content in log messages:
On the Central Log tab select Message in the Add Filter list box. Type a search string in Contains or
an exclude string in Doesn’t Contain and Click on the Filter button
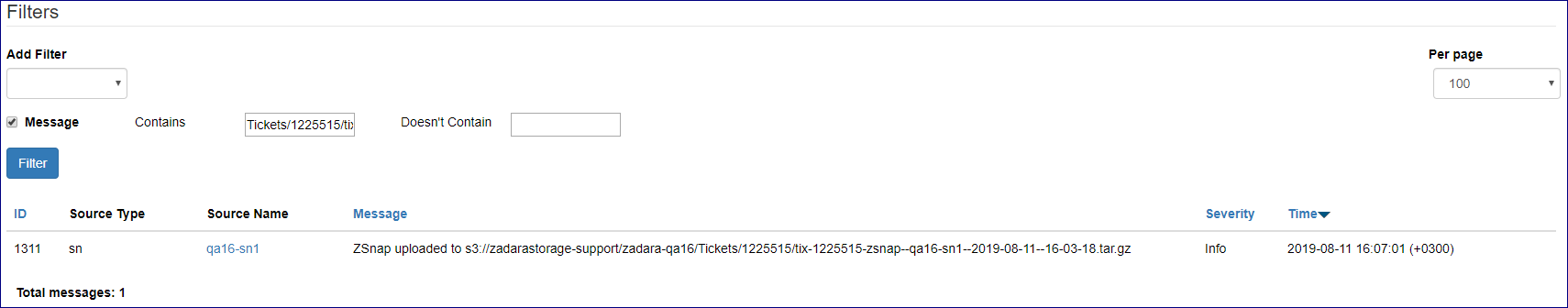
Additional filters can be applied can be applied by selecting more statements in the Add Filter list box.
Users can filter log messages by:
Statement |
Description |
|---|---|
Message |
Search\exclude string |
Created |
Event creation date range |
Min Severity |
Minimum severity level |
Source Type |
Element in which event occurred (Storage Node, VPSA, etc. ) |
Source Name |
Selection\exclusion of a specific element |
Note
Filter statements have a “logical and” relationship between them
Forwarding Events To A Syslog Daemon¶
To forward cloud events events to an external syslog daemon:
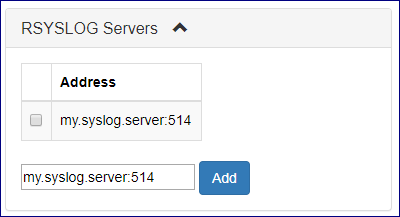
On the Central Log tab select click on the RSYSLOG Servers caption. In the text box below type your syslog server IP address and the syslog daemon port number separated by “:” .
Click on the Add button to apply changes.
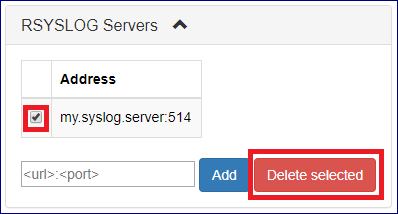
To stop forwarding cloud events events to a defined syslog daemon:
On the Central Log tab select click on the RSYSLOG Servers caption. Select the checkbox for the specific syslog daemon server you would like to remove
and click the Delete selected button.
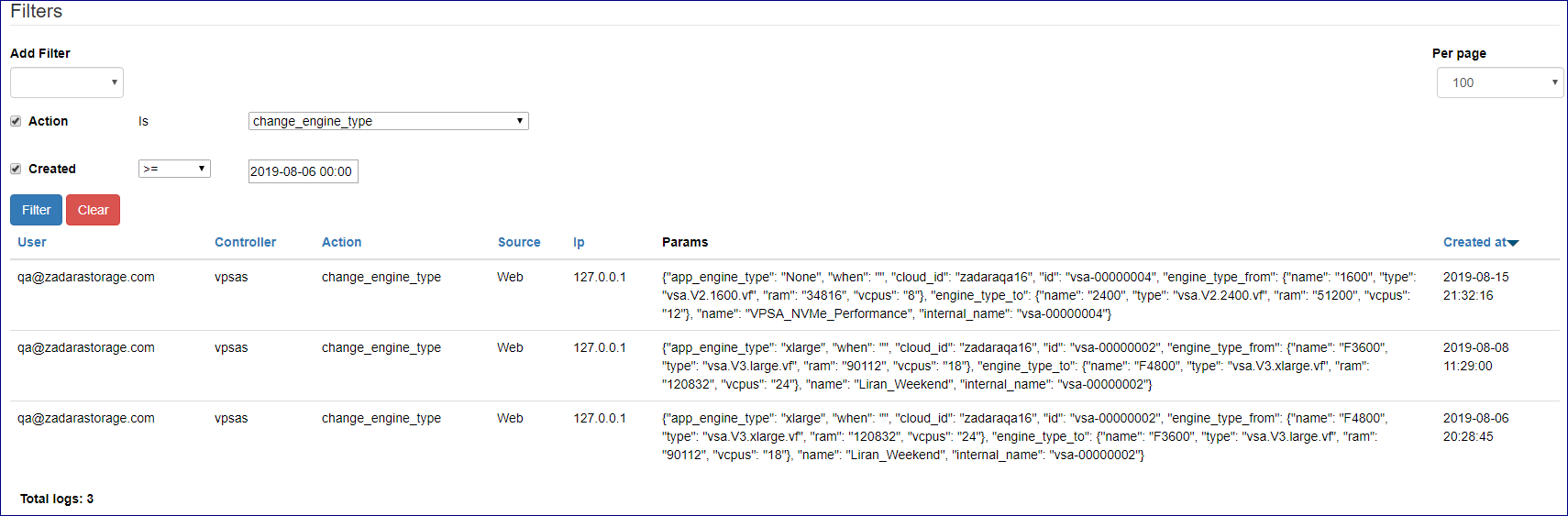
Managing Command Center Access Log¶
To view command center access log click on the  icon on the top right side of the screen and select
Access logs from the drop down menu.
icon on the top right side of the screen and select
Access logs from the drop down menu.
Access log messages can be filtered in a similar way as with cloud central logs.
Available filter statements are :
Statement |
Description |
|---|---|
Action |
Command center Action performed or attempted |
Access Type |
Web or API access |
IP Address |
Originating IP address |
User |
Originating User ID |
Created |
Log record creation date |