Central Log
Command Center maintains a centralized cloud-level event log, which can be used for detailed infrastructure monitoring and troubleshooting.
Logged events can be viewed and searched from Command Center’s Central Log option on the left navigation tree.
Events can also be exported to an external syslog daemon for 3rd party application-based event monitoring.
Searching and filtering logs
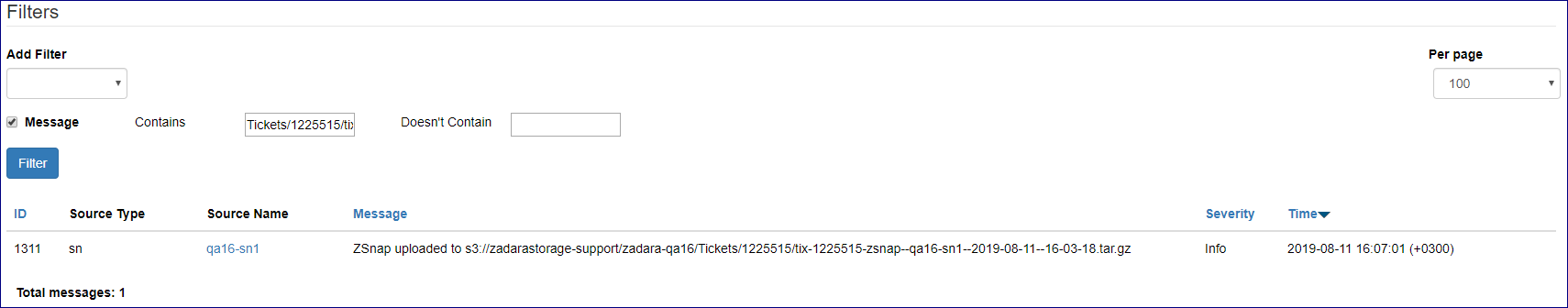
Cloud logs can be searched and specific events extracted, using the Command Center filtering functionality.
To view and search for specific content in log messages:
Click Central Log on the left navigation tree.
In the Central Log view, click in Add Filter to display its dropdown, and select and configure one or more filters to narrow down the log events search:
Message:
Contains: A case-insensitive string that matches searched log entries.
Doesn’t Contain: Exclude log entries that match this case-insensitive string.
Created:
From the dropdown select the log entry’s creation date’s relational operator:
>=: On or after date and time (inclusive). Select the date and edit the time. The search will return matching log entries created on or after the entered date and time.
<: Before date and time (exclusive). Select the date and edit the time. The search will return matching log entries created before the entered date and time.
Between: A period specified by a starting date and time, and an ending date and time. Select the start and end dates, and edit the time for each. The search will return matching log entries created on or after the starting date and time, and before the ending date and time.
Min Severity:
The search will return all log entries that match the selected severity level, or have a higher severity level.
Severity levels, listed from high to low:
Emergency - highest severity level
Alert
Critical
Warning
Error
Notice
Info
Debug - lowest severity level
Source type: The component type for which the log event was generated:
sn: Storage Node
vpsa: VPSA
zios: Object Storage VPSA
ccvm: Command Center
Source name: The name of the component for which the log event was generated:
Enter only one of:
Is: The search returns only the log events for the specified component.
Is not: The search excludes the log events for the specified component, and returns all others.
Click Filter.
Note
Filter statements have a logical “and” relationship between them.
All filters are optional.
Forwarding events to a syslog daemon
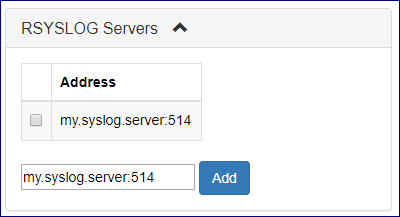
To forward cloud events to an external syslog daemon:
Click Central Log on the left navigation tree.
Narrow down the log events to export, by Searching and filtering logs.
Click the RSYSLOG Servers caption.
In the text box, enter the syslog server’s IP address and the syslog daemon port number, separated by a colon:
<url>:<port>.Click Add.
Stop forwarding events to a syslog daemon
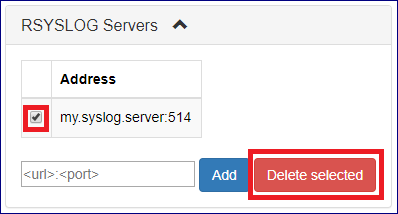
To stop forwarding cloud events to a defined syslog daemon:
On the Central Log tab select click on the RSYSLOG Servers caption.
Select the checkbox for the specific syslog daemon server you would like to remove
and click the Delete selected button.
Click Central Log on the left navigation tree.
Click the RSYSLOG Servers caption.
Mark the checkbox of the syslog daemon server to remove.
Click Delete selected.